Yuppp.. lama ya tidak share exploit deface. Kali ini saya mau share tutorial deface WordPress dengan Exploit Themes Qualifire File Upload Vulnerability . Exploit nya sudah lama sih sebenarnya, namun gak tau kenapa sekarang “bersemi kembali” . Oke gak usah lama lama , langsung saja .
Bahan :
HTML Exploit : download
Google Dorks :
- inurl:”/wp-content/themes/qualifire”
Use your brain, bitch !
Vuln : /wp-content/themes/qualifire/scripts/admin/uploadify/uploadify.php
Simpan exploit di atas dengan format .html. Jangan lupa ganti url nya dengan url target.
Setelah itu buka file exploit nya di browser.
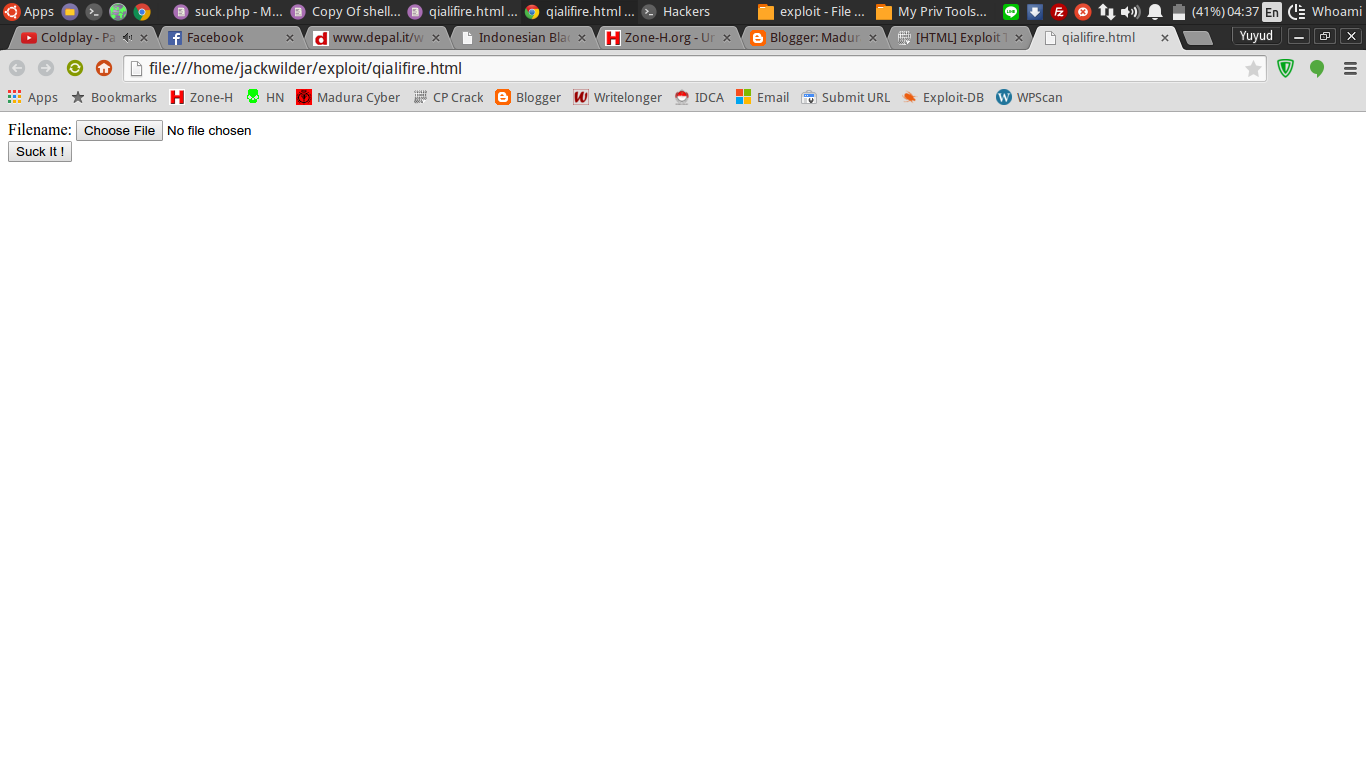
Shell kalian akan berada di localhost/shell.php
Karena langsung berada di public_html, jika kalian hanya ingin deface, bisa langsung upload script.

Sekian tutor Deface WordPress dengan Exploit Themes Qualifire File Upload Vulnerability kali ini, happy exploiting.
Not found gan pas dah selesai upload di html explo